Last Updated on July 4, 2024 by Team Experts
There has been a tremendous increase in the number of data breaches. Hackers are using the latest advancements in technology to carry out their nefarious acts. As the risk of cyberattack increases, businesses are spending considerable amounts to quell the menace. According to Grand View Research, the global cybersecurity market was estimated at US$ 167.13 billion in 2020. It is expected to grow at a CAGR of 10.9% between 2021 and 2028.
Businesses have gradually woken to the fact that communication with their customers’ needs to be protected. One of the key statistics that can stand testimony to the hacking menace is that personal data was involved in around 58% of the breaches. But how to protect data in transit? We will learn this and more in this article.
What Is Data in Transit?
When an internet user enters the website address on the browser of his device, data is in transit that traverses the internet as you are trying to connect to the website. It is essential to understand that communication exchange happens as you are interacting with the site. The data that is travelling across the various networks must be protected.
It also covers the email exchanges that are happening throughout the day. Every day, email users send and receive several emails, and this exchange of information must be secured. The data in transit is protected by encrypting the data using the Public Key Infrastructure (PKI).
How encryption ensures data security?
Encryption is powerful in the sense that it transforms the data into an indecipherable format that the authorized recipient of the information can only access. In actual terms, only the desired sender and receiver have access to the data, thereby mitigating the risk posed by hackers. The technology acts as a line of defense to protect the data in transit and helps businesses stay protected and compliant with regulations about data protection.
Encryption utilizes different algorithms that are used to encrypt data. Over time, there have been improvements in the algorithms, and the current algorithms provide ample opportunities to ensure the integrity and confidentiality of data. In addition, it can restrict data access, and the advances in cryptography have ensured that it has several different uses in real life.
It is a privacy safeguard that can increase trust as businesses can showcase their clients’ security of their data protection systems. Weneedprivacy is used to know the Internet in your daily activities and realizes the value of your privacy. Studies have shown that poor data quality has prevented companies from gaining the full potential of data lying with them. Data integrity can help secure high-quality information, which will help understand customer demographics, tracking trends and behavior of the audience.
HTTPS helps in securing data in transit
Earlier, internet communication was being done using the HTTP protocol. However, it was vulnerable to data breaches as there were several loopholes in the technology. Gradually, cybersecurity systems moved to the HTTPS protocol. It is possible by using an SSL/ TLS certificate that tackles this menace by encrypting the information that is exchanged.
Transport Layer Security (TLS) powers encrypting the data in transit and are the cryptographic protocol that helps secure internet communication, email exchanges, etc. It ensures that the data is not tampered with while in transit and the communication originates from genuine sources. HTTPS, The certificates are provided by authentic third-party Certificate Authorities (CAs). The CAs provide these certificates after a preset validation process based on the chosen type of certificate.
The use of SSL certificates
If you wish to move your website to the HTTPS protocol, you must install an SSL certificate. The advanced Transport Layer Security (TLS) protocols are used in the certificates. Now the question arises – Why are they called SSL certificates? The terminology has remained, and there is no need to panic and change your certificate.
It comprises data files that are hosted in the webserver. In addition, there is a public-private key pair that ensures encrypted communication with the visitor’s browser. The use of these certificates also provides a sense of trust in the visitors’ minds. The Certificate Authorities (CAs) undertake validation of the website and the business based on the type of certificate selected.
If you are yet to move to the HTTPS platform, all you have to do is install an SSL certificate. Depending on your online venture, you need to select the perfect SSL certificate for your business. If you own a single domain, the standard single domain certificate will be suitable for you. However, a wildcard SSL certificate will be more appropriate for your business, as it affords protection to your chosen primary domain and multiple first-level subdomains under it.
Wondering which brand to go for? There is a plethora of options to choose from such as GlobalSign, Thawte, Comodo, RapidSSL certificate, etc. However we suggest that you take your pick from reliable provider or reseller such as ClickSSL. They not only provide you with premium SSL certs at cheap prices but also have a reliable after-sales support system.
How SSL help in data transit?
When the browser tries to connect to a website that has installed an SSL certificate, it requests the server for identification. The web server sends a copy of the certificate to the browser. The browser now checks whether the certificate can be trusted and sends a message to the server accordingly. The web server sends out a digitally signed acknowledgement for starting an SSL-encrypted session.
Checking if a website has an SSL certificate
Understandably, visitors must only visit websites that have installed an SSL certificate. But how to check if a site has an SSL Certificate? As a first step, you must check the padlock on the address bar. In some cases, the website may have mixed content. Therefore, it is also suggested that visitors avoid visiting such websites.
For additional information, the visitor must click on the padlock. There will be a pop-up, and you must now click on the “Certificate (Valid)” tab.

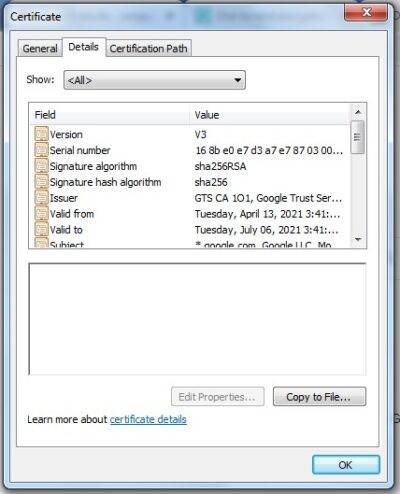
When you click on that tab, a new window will open. Next, click on the “Details” tab for additional information about the certificate.
The “Valid From” field in the “General” tab will throw light on the certificate validity.
Additional measures to protect data
Below are listed some additional measures to protect your data.
Using an access control software
Businesses must ensure there are adequate network control mechanisms in place to ensure the protection of underlying data. Investing in a feature-rich antivirus that comes with an advanced firewall can prevent data breaches. The use of anti-malware software can secure networks against malware or other intrusion methods adopted by hackers.
Using data protection solutions
These solutions can aid businesses through policies that can ensure that it ensures encryption of sensitive data automatically. It can also ensure blocking the transfer of sensitive data based on preset criteria. You must also categories sensitive data based on where it is stored. It will help you to deploy adequate security measures based on this categorization.
Using advanced software to detect anomalies
The advancements of artificial intelligence technologies help to assess behavior about data access and assess underlying risks. The security analytics tools provide insights on how to prevent data loss. It provides adequate visibility to users without being bogged down by too much use of administrative resources.
Conclusion
HTTPS: Businesses must ensure that the customer data is protected at all costs. It ensures customer trust and prevents hefty penalties from government authorities. But how to protect data in transit? All you must do is encrypt the stored customer data. Then, you can classify the data according to the risk profiles and take adequate steps to protect them from hackers. Internetbeskyttelse, where you can protect your data
The use of SSL certificates acts as a crucial factor in your cybersecurity setup. It can undertake a whole set of activities by encrypting the communication with the visitor’s browser and ensures security to data in transit.
Also read about: Tips to Maximize Your Online Business Success

